Stapler is a “boot to root” VM hosted on the Vulnhub website. Boot to root challenges are designed for penetration testers and hackers who want to build their skills and have fun at the same time. The goal is to find a way to hack into the virtual machine, get...
[Read More]
FISMA and NIST Notes
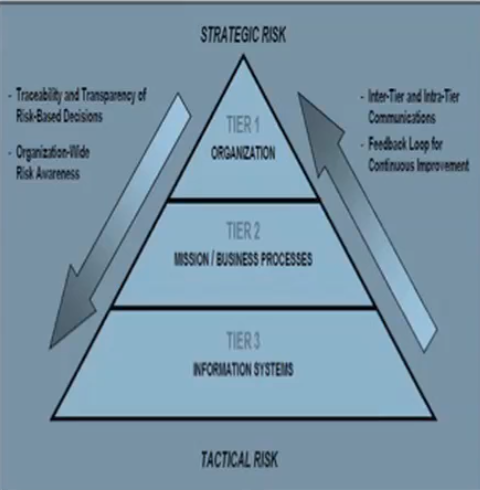
Focus - Risk Management Framework
FISMA: Federal Information Security Management Act Standards used by ALL federal agencies to categorize all information and information systems based on risk levels. Guidelines recommending the types of information and information systems to be included in each category. Minimum information security requirements (management, operational, and technical controls). Defines three objectives:...
[Read More]
Insight into SecOps
Purple by default
Taking a break from our regularly scheduled Microsoft deep dive, I bring you some insight into daily Security Operations. In a world where we’re hired to be a traditional blue teamer, if we have the drive, we often have the opportunity end up becoming a purple teamer (Red + Blue!)...
[Read More]
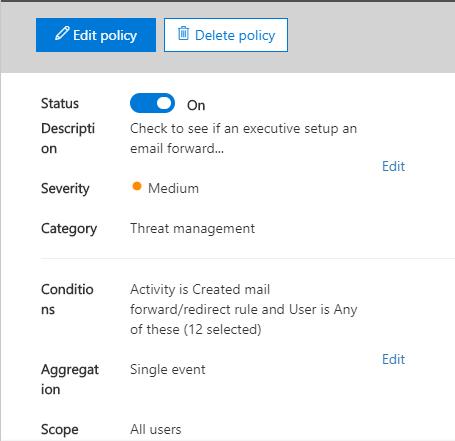
O365 Security and Compliance Monitoring Rules
Rule types, creation, and recommendations
Continuing on where we left off during our overview of the Security and Compliance center, we return to explore the capabilities contained within the default alerting structure, and the flow of how to create custom alerts. Let’s dive right in.
[Read More]
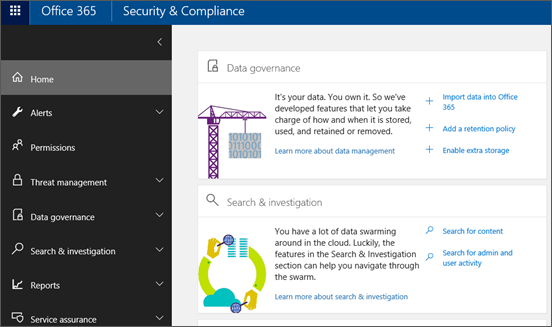
Microsoft O365 Security and Compliance Center
Overview - The first of many
Over the next few blog posts I will be exploring some of the capabilities and features on the long list of security products that Microsoft offers. First on the list is the overview of the Security and Compliance center in Office 365, the next post will focus on exploring the...
[Read More]